The size of a single packet or group of packets can tell you a lot about a situation. Under normal circumstances, the maximum size of a frame on an Ethernet network is 1,518 bytes. When you subtract the Ethernet, IP, and TCP headers from this number, that leaves you with 1,460 bytes that can be used for the transmission of a layer 7 protocol header or data. With that knowledge, you can begin to use the distribution of packet lengths in a capture to make some educated guesses about the traffic.
Importing the file download-slow.pcap will provide a great example of this. Once the file is imported, switch to summary tab, you will see the result in Figure 5-10
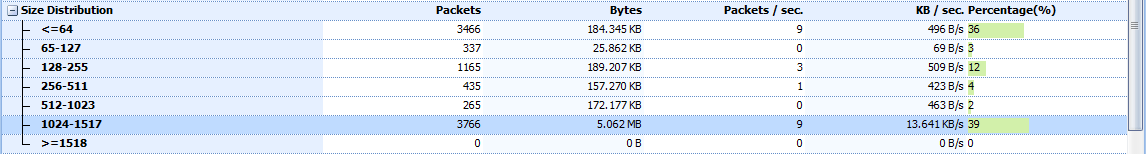
Figure 5-10: The Packet Size distribution helps you make educated guesses about the traffic in the capture file.
I’ve highlighted the section showing statistics for packets ranging from 1024 to 1517 bytes in size. Larger packets such as these typically indicate the transfer of data, whereas smaller packets indicate protocol control sequences. In this case, we have a fairly large percentage of large packets (39 percent). Without even seeing the packets in the file, we can conclude that the capture file contains one or multiple transfers of data. This could be in the form of an HTTP download, an FTP upload, or any other type of network communication where data is transferred between hosts.
Most of the remaining packets (36 percent) are less than 64 bytes range. Packets in this range are usually TCP control packets that don’t carry data. Let’s consider the typical size of protocol headers. The Ethernet header is 14 bytes (plus a 4-byte CRC), the IP header is a minimum of 20 bytes, and a TCP packet with no data or options is also 20 bytes. This means that standard TCP control packets—such as SYN, ACK, RST, and FIN packets—will be around 54 bytes in size and fall in this range. Of course, the addition of IP or TCP options will increase this size.
Examining packet lengths is a great way to get a bird’s-eye view of a capture. If there are a lot of large packets, it may be safe to assume that data is being transferred. If the majority of packets are small, you may assume that the capture consists of protocol control commands, without a great deal of data being passed. These are not hard-and-fast rules, but making such assumptions is sometimes safe before taking on deeper analysis.